Mobile phones have become an inseparable part of our lives. Across the globe, mobile phone users use the phone for online shopping, bill payments, ordering groceries, and more. Though app developers must focus on the functionalities of the app, it is equally important to focus on the security aspects of the app.
As per a survey, close to 98 percent of the apps are not completely secure. This is an alarmingly high number since the private data of the app users could be at stake. Hence, mobile app development companies must make app security testing a part of the DevOps and testing lifecycle.
Companies must move away from the mindset where security testing is pushed to the end of the development lifecycle. All the essential security checks must be performed before the changes are made live on the production server. It is recommended to partner with a mobile application testing company in scenarios where you do not have an inhouse security testing team.
In case you are on the lookout for a detailed checklist to get started with security testing, look no further since we have it all covered in this blog. The learnings of this blog will be helpful in devising a security testing strategy for your mobile app.
State Of Mobile App Security
As per the State Of Mobile report[1] by Data.ai, close to 4.35 Lakh app downloads are performed every minute. Daily time spent by users has also risen to 4.8 hours in 2021.
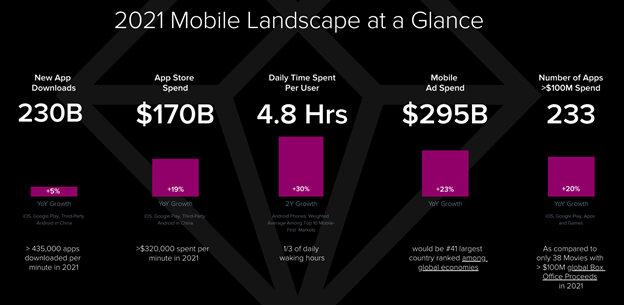
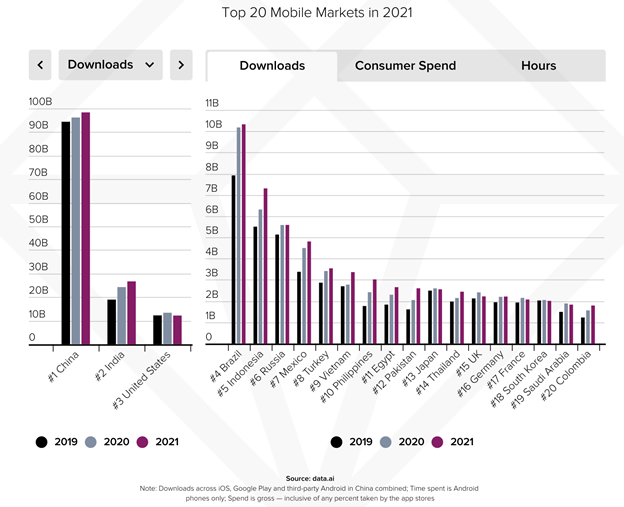
Though mobile apps have been widely used across the globe, issues still lie with security aspects of many mobile applications. One out of thirty-six apps are not completely secure for end usage. This is an alarmingly high number and the only resort to bring down this number is by relentlessly focusing on improving the app’s security.
Since app security is of prime importance, many companies opt for mobile app testing services for ensuring that mobile applications are tested in a rigorous manner. As far as mobile apps are concerned, they are primarily categorized as:
- Native Apps – Apps that are built using the SDK offered by the respective mobile OS (i.e. Android or iOS)
- Hybrid Apps – Apps with look & feel of native apps but behave like web apps, thereby taking the advantage offered by both the app types
- Web Apps – Apps that are built using HTML and accessed from the mobile web browsers. These are desktop apps that are tailor-made for the mobile viewport
Also Read – Introduction to API Security Testing
Mobile App Security Issues in Android & iOS
Security issues that you would encounter in Android apps might differ from those witnessed in iOS apps. Well, they are two different operating systems – Android is open-source whereas iOS is closed-source.
Many OEM manufacturers add changes to the Android mainline code at different levels (e.g. kernel, middleware, UI) to have a differentiating factor from the competitors. As an Android app developer, it is recommended to opt for native apps if the app needs access to the device capabilities like camera, GPS, sensors, etc.
Now that we have the platform set, let me walk you through the different security issues in Android and iOS.
Mobile App Security Concerns in iOS
It is a well-known fact that iOS apps go through a much wider scrutiny by the apps team before they are made live on the iOS store. However, it might be incorrect to say that iOS apps are not vulnerable to security attacks.
As per OWASP[2], here are the top 10 security concerns observed in iOS applications:
- Improper Platform Usage
- Insecure Data Storage
- Insecure Communication
- Insecure Authentication
- Insufficient Cryptography
- Insecure Authorization
- Client Code Quality
- Code Tampering
- Reverse Engineering
- Extraneous Functionality
Mobile App Security Concerns in Android
Contrary to iOS applications, Android apps are more vulnerable to security threats. The app screening process to get listed on PlayStore is not so stringent compared to iOS (or iTunes) store.
Some of the major security concerns observed in Android applications[3] are:
- Social Engineering
- Data leakage through malicious applications
- Spyware
- MITM (Man-in-the-Middle Attacks)
- Permission issues
- Phishing and malvertising
To identify security issues in the mobile applications, it is important to devise a detailed Vulnerability Assessment plan and Security Testing & Pentesting plan.
Also Read – Android Vs. iOS Mobile App Testing
Detailed Mobile Security Testing Checklist
Here are the major pointers that must make way into the security testing checklist:
1. Perform Security Audit
This is the very first step in identifying security issues in the mobile application. As a QA engineer, you need to know the purpose and depth of the audit. For example, if the application is using third-party APIs, you need to make sure that the data is secure whether it is in transit or at rest.
Since there would be multiple areas of security that need to be looked into, you should prioritize the ones that need immediate attention. Authentication and authorization, access permissions, data storage, and cookies are some of the areas that should be looked into at a high priority.
The audit must include the ways to mitigate different types of security threats, along with covering ways in which such security issues can be looked into at early stages of the development & testing cycle.
2. Threat Modeling and Assessment
As mentioned in OWASP[4], threat modeling is the process of identifying, communicating, and understanding the threats & mitigations within the context of protecting something of great value. In case of mobile applications, threats could be from third-party interactions (e.g. third-party APIs or interactions with third-party servers) or it could be security threat due to poorly designed app architecture.
At this stage, team members need to wear the hats of attackers & users and exploit the security vulnerabilities from all angles. Usage of automated tools like ADB (Android Debug Bridge), MobSF (Mobile Security Framework), and iMAS (iOS Mobile Application Security) can be used for performing automated security tests on Android & iOS applications.
Threat modeling and assessment is an integral step since it helps in realizing a risk-based analysis of the bug priority and its impact. It is an integral part of the mobile app security testing checklist.
3. Security Exploitation
In the previous step, you identified (or assessed) the potential vulnerabilities. Now is the time to use the appropriate pentesting or security testing tools to exploit different vulnerabilities in the app.
Performing this step is critical since it ensures that the security vulnerabilities do not make it to the app that will go live on the app store. QARK (Quick Android Review Kit) and ZAP (Zed Attack Proxy) are the widely used mobile app security testing tools.
In case your team is not experienced enough to use these tools, it is advised to onboard an experienced mobile testing services company like KiwiQA that has the experience of working with a wide range of clients.
4. Fixing Vulnerabilities
By the end of this step, you would have identified the vulnerabilities and even tried to exploit the same. The security vulnerabilities must be divided in different priority buckets so that you (and the team) can patch the security issues as per the priority.
Now, you should have a well-tested app that has been tested well from a security standpoint.
Also Read – Guide To Mobile Application Security Testing
Conclusion
In this blog, we deep dived into the essential aspects of mobile app security testing. Testing the mobile app from a security perspective is important for ensuring customer stickiness. It avoids scenarios of any potential data leaks where vital confidential (or personal) information is accessible to an untrusted environment.
To make the most out of security testing, many developers and enterprises onboard an experienced mobile app testing services company in order to release a more secure mobile app in the respective store.










Comments are closed.