Mobile phones and mobile applications have an indispensable part of our lives! Mobile apps offer convenience, personalized experience, greater accessibility, and improved user experience – factors that are normally not possible with normal websites.
At the time of writing this blog, iOS accounted for ~27.6 percent share[1] whereas Android dominated with 71.8 percent of the mobile operating system market. Though Android leads the race by a huge margin, iOS apps have a significant higher revenue when compared to Android apps. In 2021, users spent close to $85.1 billion on iOS apps as compared to $47.9billion on Android apps!
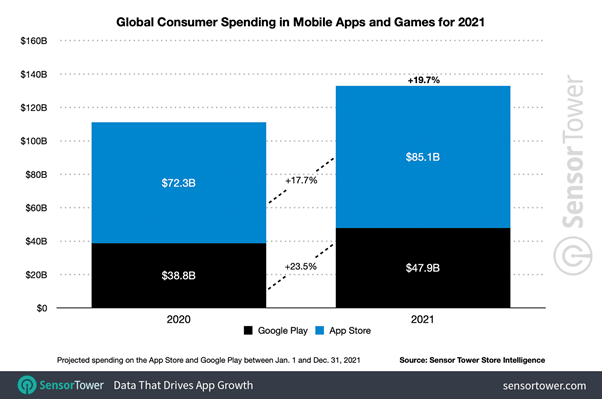
Android and iOS apps revenue comparison
However, many application users fall prey to online attacks whereby malicious actors/hackers might gain illegal access to your data, device, etc. For instance, hackers were able to exploit the zero-day vulnerability (CVE-2022-32917) in iOS though which they were able to execute rogue computer code iPhones with kernel privileges[2].
Since consumer’s data and company’s reputation is at stake, companies (i.e. OS providers like Apple, Google) release software patches to fix the vulnerabilities. In terms of security, iOS apps are considered to be more secure than Android apps since Apple has so far operated the iOS store as a closed-walled garden. As per reports, Apple is planning to open up its walled garden in 2023[3] which means that users might be able to side-load apps in iPhones as well 🙂
Since the use of iOS is on a continuous rise, it is important to focus on the security aspects of the application. Digital businesses (B2B, B2C, B2D, B2B2C) must focus heavily on security testing of the app so that they can ship a fully-functional highly-secure app to the users! Onboarding a security testing company with experience in serving customers from different segments can turn out to be a huge benefit in bolstering the security testing efforts.
In this blog, we deep dive into the tips & tricks that should be a part of the iOS security testing checklist. The learnings of this blog can act as a go-to guide to security testing of iOS applications. Do, let’s get started…
Security Challenges With iOS Applications
As mentioned earlier, iOS apps are considered to be more secure and less vulnerable to data thefts (or leaks) when compared to their Android counterparts. It is important to note that all third-party iOS applications (i.e. apps that are not available out-of-the-box in iPhones) are sandboxed[4].
Hence, the apps will not be able to modify/access files stored by the other apps. Also, these apps are restricted from making any changes in the device settings.
Having said that, here are some of the major challenges that iOS developers can face when comes to security of the apps:
Network Security
Any type of iOS application will require some interaction over the network. Whether it is a gaming/banking/e-commerce application, it would still require connectivity with the back-end (or database).
Apps in the domains like fintech and banking domains might transmit sensitive information (e.g. username, account details, etc.) over the network. As a principle, the data must follow the best encryption standards so that only authorized personnel are able to decrypt the same on the recipient side. It is recommended to always follow secure communication protocols like SSL (Secure Socket Layer) to establish an encrypted link between the client and server.
As an iOS app developer, you must follow the right security protocols for ensuring that data is always secure – whether it is in transit or at rest!
Also Read – Network Penetration Testing: What, Why, and How
Input Validation
No unverified or unvalidated data must get into the back-end. Your app might have input forms but the data being entered by the users must be validated before being sent to the server.
Apart from this, the app might be receiving data from external sources (e.g. network requests). Network requests must be secure so that the app is not vulnerable to injection attacks.
As an iOS app developer, any type of data (including input characters) or external request must go through validation cycle at the front-end and/or back-end.
Insecure Storage
Any type of app will need to store some data on the device’s storage (or cache). This stored information will be helpful in boosting the app’s startup time as well as its performance.
Any leakage of data can lead to financial losses to the respective user of the app. Along with validating the input, developers have to make sure that the data (irrespective of its sensitivity) must be secure & encrypted all the time. This minimizes the probability of vulnerabilities in the app.
Use of broken cryptographic algorithms
Till now you would have realized that data (in any form) must be secure whether it is in transit or at rest. iOS apps make use of cryptography for securing the data. However, the hardest part is choosing the best cryptographic libraries for usage in the app.
You need to have the right understanding about cryptography and the features of the available cryptographic libraries. Make use of strong hashing functions or strong ciphers[5] for fixing insecure use of cryptography.
iOS Application Security Testing Checklist
Now that we have looked into some of the most important security challenges that need to be addressed on priority, let’s deep dive into the items that need to be there in the checklist.
Keychain for sensitive data storage
The keychain services API provides the flexibility to the app developers through which small bits of user data (e.g. passwords, keys, certificates, etc.) can be stored in an encrypted database called a Keychain.
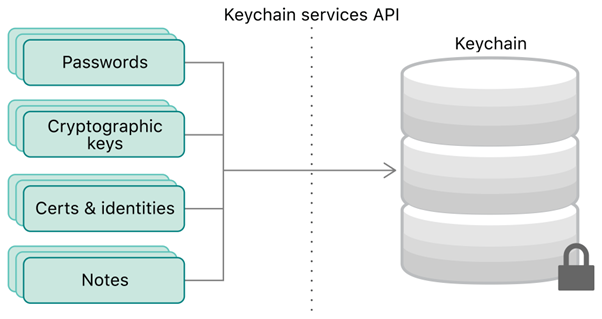
Keychain Services API
Sensitive customer data like credit card information can also be stored in keychains. Access to other apps in the device is restricted via ACL (Access Control Lists) or Keychain Access Groups for items that are synchronized via the iCloud.
The encryption mechanism used by Keychain is compromised on jailbroken devices, which is why Apple does not recommend iPhone users to avoid jailbreaking devices[6]. You can find more information about keychains in official Keychains API documentation.
Enforcing App Transport Security
Networking feature called App Transport Security (ATS) was introduced by Apple post the release of iOS 9. The feature greatly improves the privacy and integrity of iOS apps and app extensions.

App Transport Security Overview
The mandatory requirement is that network connections made by the app are secured via the Transport Layer Security (TLS) protocol. This is achieved using ciphers and reliable certificates. As per ATS, every connection must mandatorily use HTTPS and TLS1.3.
ATS blocks all the network connections that do not meet the basic security requirements. You can find more information about keychains in official App Transport Security (ATS) documentation.
Also Read – Your Guide To Mobile Application Security Testing
SSL Pinning
As mentioned earlier, SSL (Secure Socket Layer) supporting minimum TLS1.2 is mandated as per ATS requirements[7]. For starters, SSL ensures that all the communication between the client and server happens over a secure channel.
As app developers, it is a good practice to keep the users informed about the repercussions of using unsecured public networks. This is where SSL pinning (or certificate pinning) comes into the picture.
SSL pinning is a mechanism through which the client verifies whether it is communicating to the right server, rather than some attacker that has intercepted the communication. With SSL pinning, the communication between the client and server is always secure and the SSL certificate is pinned (or embedded) in the client application. The integral question is how does both the parties (i.e. client and server) ensure that the communication between them is secure. This is done via certificate matching process.
Whenever there is any client-server communication, the server’s certificate is compared with the certificate that is embedded in the client app. In case the certificates match, connection is secure else it is considered to be insecure. Insecure communication does not go through since the connection is automatically terminated.
SSL pinning is majorly instrumental in avoiding man-in-the-middle attack (MitM)[8] where the attacker secretly intercepts and relays messages between the client & server (who are assumed to communicate with each other). TrustKit is one of the most-popular open-source SSL pinning libraries that is widely used by iOS and macOS applications. You can find more information about TrustKit in the official documentation of TrustKit.
Also Read – Mobile App Security Testing Checklist
Debug Code
It is not a good practice to leave code with debug logs in production. It unnecessarily increases the app memory size and footprint. The bigger problem is that the code is compiled along with the API calls being used, thereby providing room for malicious actors to attack the network!
Like any other form of code, it is recommended to have Debug logs enabled under conditional compilation directives. As mentioned in Apple Developer Forums[9], Swift (language used for creating iOS apps) does not have preprocessors. As stated in the forum, it is recommended to have debug code under the #if DEBUG … #endif directives.
Check authenticity of third-party libraries
It is a common practice used by iOS developers to leverage third-party libraries for accelerating the development time. However, there are risks of using untested or insecure third-party libraries. Some libraries might even exploit vulnerabilities in the source code – a factor that will be detrimental for the application!
Hence, it is recommended to check the authenticity of the third-party libraries. You can even go further by executing sample security tests on those tools. A good practice is to verify how many popular iOS apps[10] use the said third-party library. This can be a good starting point in making a decision regarding the usage of libraries in your application.
Data Protection
As mentioned earlier, it is a good security practice to ensure that the data is always secure (be it in transit or rest). As explained before, ATS (App Transport Security) takes care of the security aspects when the data is in transit.
The NSFileProtectionComplete flag must be used to keep the data in the disk encrypted or secured all the time. As stated in the official documentation, the flag also ensures that the data is in the encrypted format even when the device is in the booting stage or locked state.
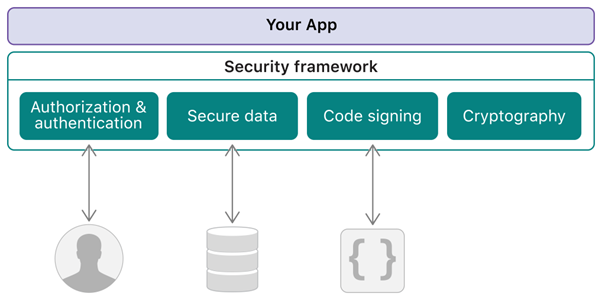
Tools to enable secure interaction with users, data, and code
The NSFileProtectionCompleteUntilFirstUserAuthentication global variable ensures that the file on the disk is in the encrypted format and can only be accessed after the device has booted. You should refer to Security framework documentation that deep dives into the security framework used for protecting information, establishing trust, and controlling access to software.
Screen Recording and Capture
Screen recording and screen capture must be mandatorily disabled for screens where users are entering personal details, credit card information, etc.
Recording or capturing activities happening on the device screen can result in serious consequences like data leak or potential misuse of information. In fact, there are a couple of iOS apps[11] that actually records what the users are doing on the screen.
Just imagine if the users are able to capture screen or record interactions when your iOS app is in use? It is a serious security concern that could shoo away users from the app. In such cases, you could use the ScreenshotPreventing – a simple wrapper that prevents screen recording and screen capture in the respective iOS app.
For integrating ScreenshotPreventing into the Xcode project using Swift Package Manager, simply add the following to the dependencies value of your Package.swift:
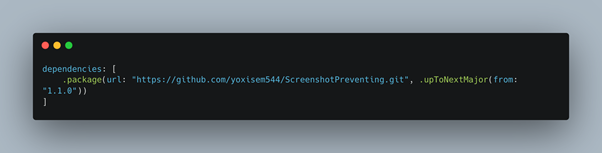
ScreenshotPreventing
Conclusion
In this detailed blog, we deep dived into some of the important security aspects that should be a part of the iOS app development and testing checklist. Security and data privacy are some of the basic requirements that your iOS app should adhere to, as any compromise could lead to data leaks and misuse of personal (or private) information.
In case you (or your team) does not have expertise with security testing, it’s best to onboard an experienced mobile app testing services company like KiwiQA. The team at KiwiQA has worked with a number of individual iOS developers and iOS development companies, whereby they could release highly functional & secure apps to their target audience.









